DNS Filtering vs. BGP Threat Mitigation
These two features work together to provide layered security:- DNS Content Filtering: Blocks access to undesirable websites based on their domain name.
- BGP Threat Mitigation: Blocks all traffic to and from malicious IP addresses, regardless of the application or port.
Phase 1: Creating a Threat Mitigation Policy
First, you create a reusable policy that defines which threat intelligence feeds you want to subscribe to.1
1. Navigate to Threat Mitigation Policies
In the SDX dashboard, go to Policies → Threat Feeds. Click + Add to start creating a new policy.

2
2. Configure Your Policy
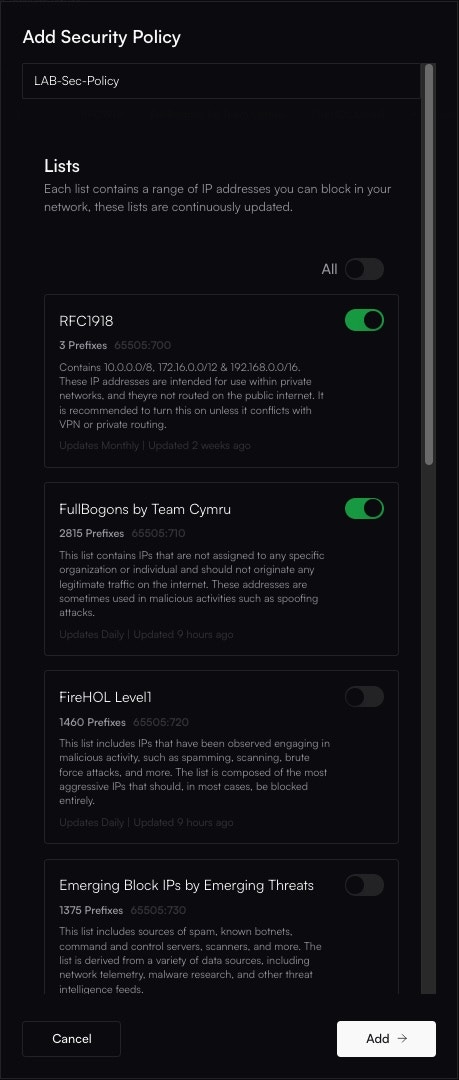
Give your policy a descriptive Name (e.g., “Standard Threat Blocking”). Then, from the BGP / DNR Lists, select the threat feeds you wish to enable. A good starting point is to enable the default feeds.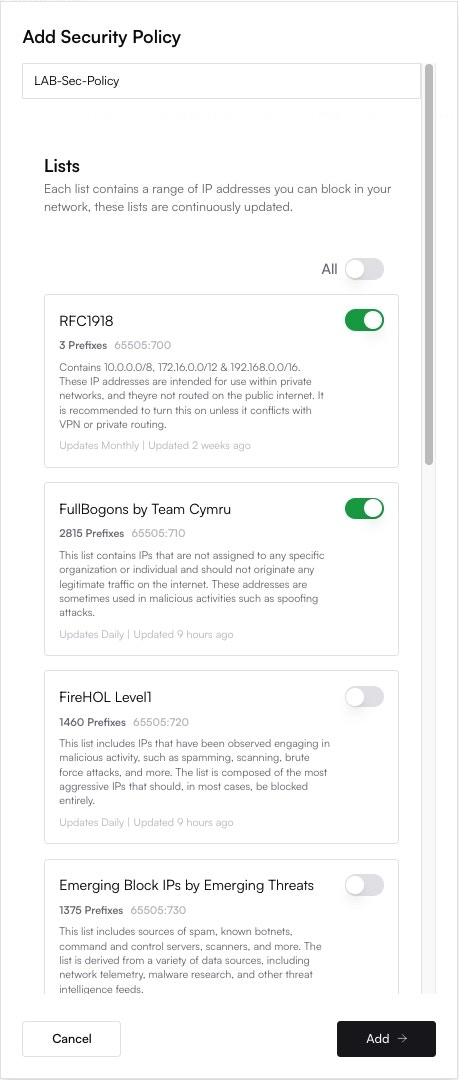

3
3. Save the Policy
Click Add to save your new policy. It is now ready to be applied to your sites.
Commonly Used Threat Feeds
Commonly Used Threat Feeds
- FullBogons (Team Cymru): Blocks unallocated or unroutable IP address space that should never appear on the public internet. Legitimate traffic will not originate from these IPs.
- FireHOL Level 1: A conservative list of IP addresses that are clearly and actively malicious. This list has a very low risk of false positives.
- Emerging Threats Block IPs: A reputable list of compromised IP addresses, command-and-control (C&C) servers, and other known threats.
Phase 2: Applying the Policy to a Site
A policy has no effect until it is assigned to a site.- Navigate to the Sites page and select the site where you want to apply the policy.
- In the site’s settings, find the Threat Feed Policy section.
- Select your newly created policy from the dropdown menu and save the changes.
Best Practices
Start with Conservative Feeds
Begin by enabling foundational lists like
FullBogons and FireHOL Level 1. These are highly reliable and have a near-zero chance of blocking legitimate traffic.Monitor for False Positives
After enabling more aggressive feeds, monitor your network for any unexpected connectivity issues. While rare, it’s possible for a legitimate IP to be temporarily listed.
Layer Your Defenses
Use BGP Threat Mitigation as your first line of defense against known bad IPs. Combine it with DNS Content Filtering to also protect against malicious or unwanted websites.