The Management VPN: An Always-On Secure Foundation
When a device connects to Altostrat, it establishes a persistent, outbound OpenVPN tunnel to our global network of regional servers. This encrypted tunnel acts as a secure, private control plane, allowing SDX to manage the device without requiring any inbound ports to be opened on your firewall.
Transient Access: Just-in-Time, Secure Credentials
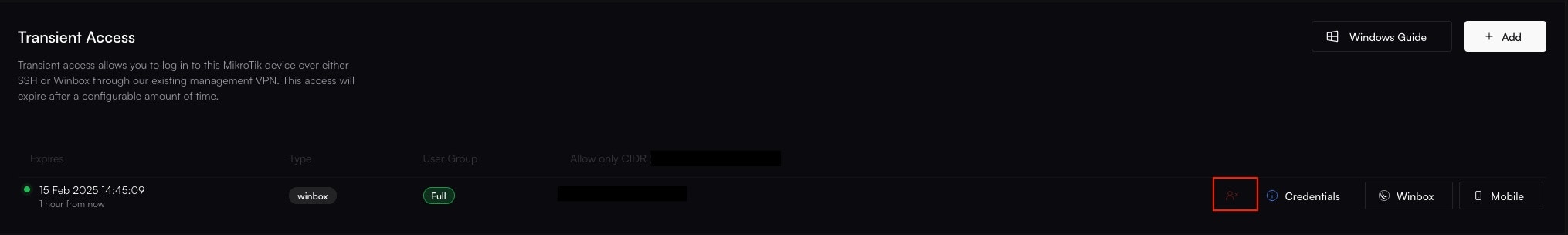
Instead of using permanent, high-privilege accounts, SDX allows you to generate Transient Access credentials. These are unique, time-limited logins for WinBox or SSH that are created on-demand when you need them and are automatically revoked when they expire or are manually terminated.
How It Works: The Secure Connection Flow
Your remote session is securely proxied through the Altostrat SDX cloud infrastructure. When you request access, the platform orchestrates a series of asynchronous jobs to build and tear down a secure, temporary pathway to your device.- Request: You initiate a Transient Access request from the SDX dashboard.
- Generation: The platform generates a unique username, a strong random password, and selects a random high-numbered port (e.g.,
48152) on the appropriate regional server. - Orchestration: Two asynchronous jobs are dispatched:
- Job 1 (Regional Server): A job is sent to the regional server responsible for your device’s Management VPN. It creates a temporary, secure NAT rule that maps the public-facing random port to the private IP address of your device’s management tunnel.
- Job 2 (Device): A second job is queued for your MikroTik device. The next time it checks in (usually within seconds), it receives a command to create a temporary user with the generated credentials and appropriate permissions (
read-onlyorfull).
- Connection: You use the provided credentials to connect to the regional server’s public endpoint on the assigned port. The server securely proxies your connection through the Management VPN directly to your device.
- Revocation: When the session expires or you manually revoke it, corresponding jobs are dispatched to delete the temporary user from the device and tear down the NAT rule on the regional server, leaving no trace of the access path.
How to Generate Transient Access Credentials
This guide walks you through generating on-demand credentials to connect to your device via WinBox or SSH.1
1. Navigate to Your Site
From the Altostrat SDX dashboard, select Sites from the main menu and click on the site you wish to access.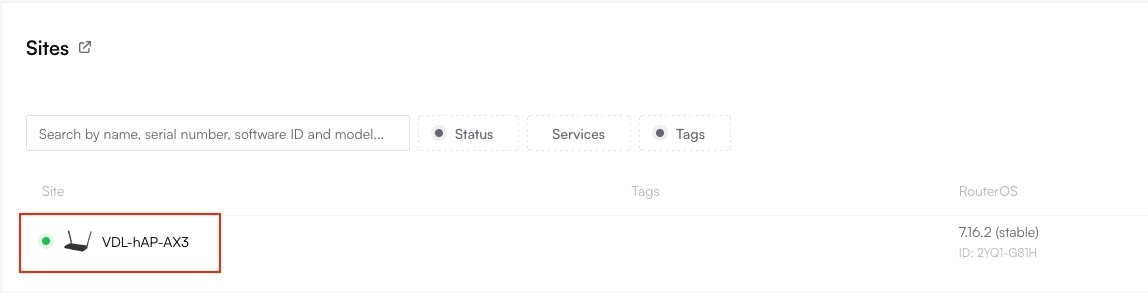

2
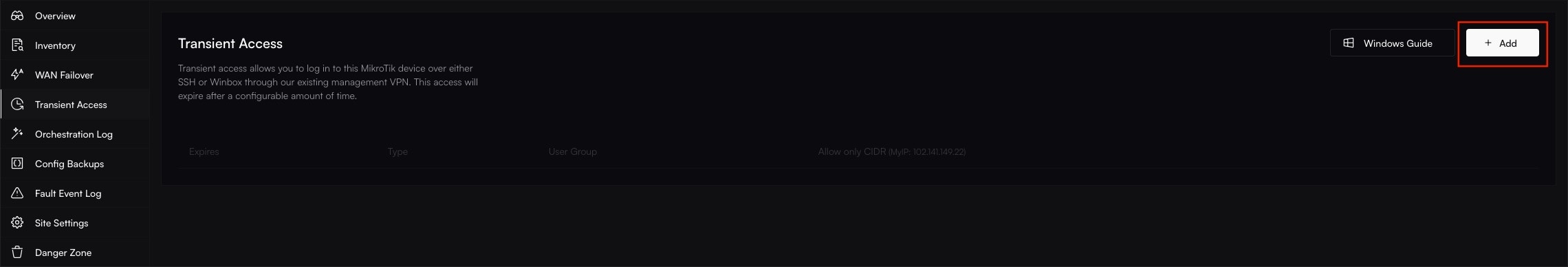
2. Open the Transient Access Menu
In the site overview, click on the Transient Access tab. This will display a list of any currently active sessions. Click the + Add button to create a new session.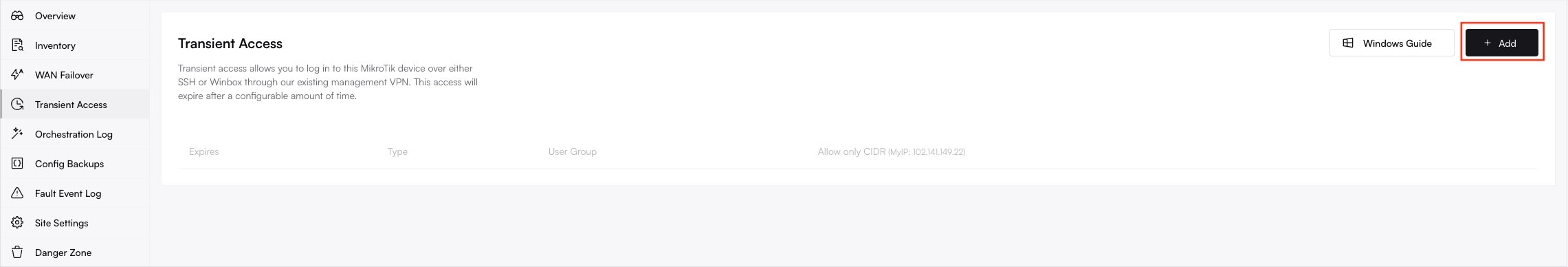

3
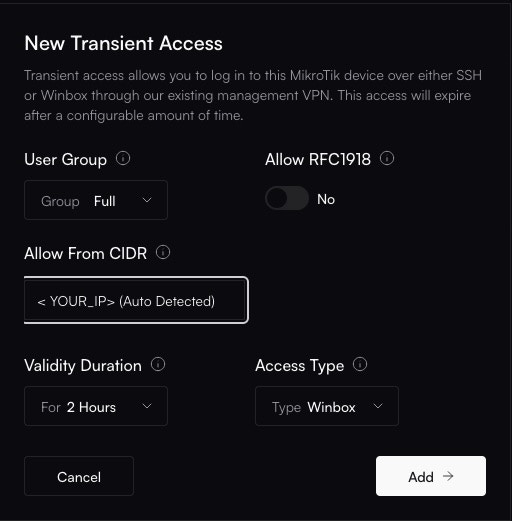
3. Configure and Generate Credentials
Configure the access parameters for your session: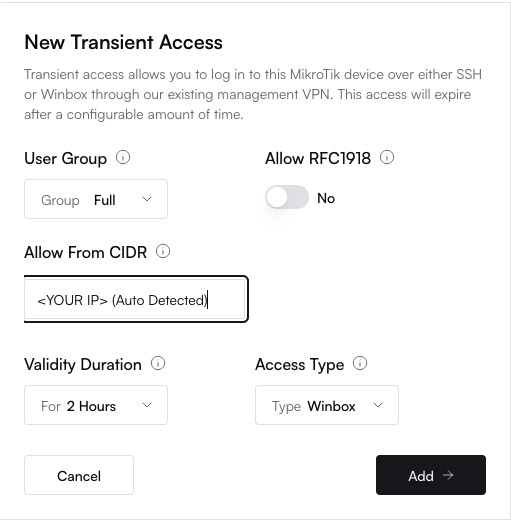
- Access Type: Select
WinBoxorSSH. - Permissions: Choose
Fullfor administrative rights orRead Onlyfor viewing configuration without the ability to make changes. - Source IP (CIDR): For added security, this field defaults to your current public IP. Only connections from this IP or CIDR range will be allowed.
- Expiration: Set the duration for which the credentials will be valid (e.g., 1 hour). The maximum is 24 hours.

4
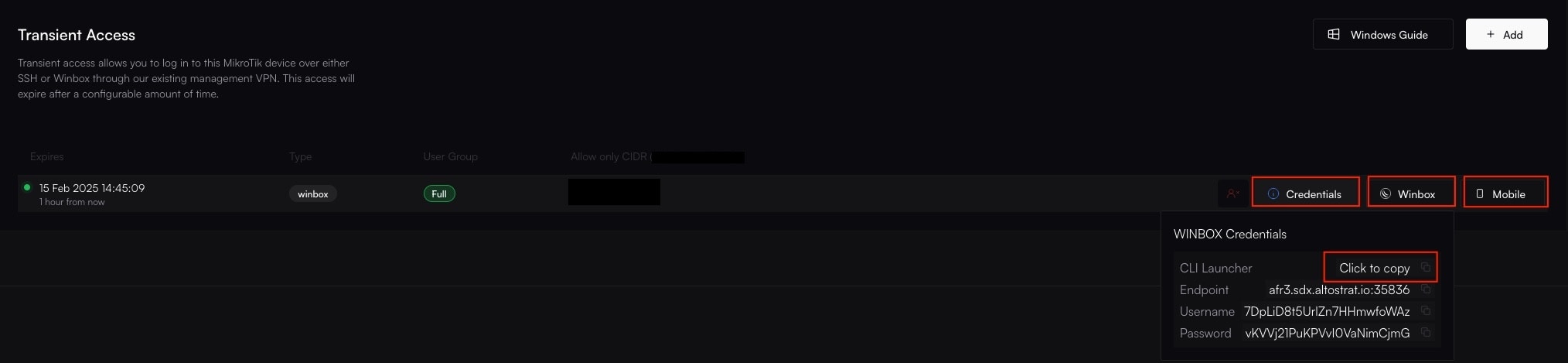
4. Connect to Your Device
SDX will display the generated Endpoint (the regional server’s hostname), Port, Username, and Password.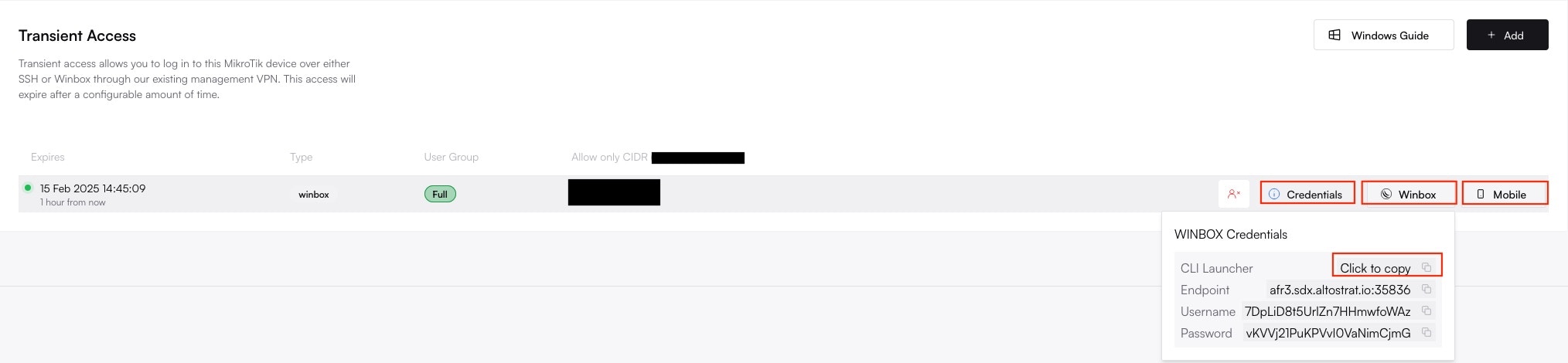
- For WinBox: Copy the credentials into your WinBox client and click Connect.
- For SSH: Use the credentials in your preferred SSH client:
ssh <username>@<endpoint> -p <port>

Managing Active Sessions
You can view all active sessions and revoke access at any time before the scheduled expiration.- Return to the Transient Access tab for the site.
- Locate the session in the Active Credentials list.
- Click Revoke to immediately dispatch jobs that invalidate the credentials, terminate the session, and remove the secure access path.

Related Feature: Transient Port Forwarding
While Transient Access is for managing the router itself, Transient Port Forwarding allows you to securely access a device on the LAN behind the router (e.g., a web server, camera, or IoT device) without a VPN.Transient Port Forwarding
Explore how to create temporary, secure port forwards to internal devices.
Best Practices
Use Short Durations
Always grant access for the shortest time necessary to complete your task. This adheres to the principle of least privilege and minimizes the attack window.
Apply IP Whitelisting
Whenever possible, restrict access to a specific source IP address or a trusted network range using the Source IP (CIDR) field. Never use
0.0.0.0/0 unless absolutely necessary.Grant Least Privilege
If a task only requires viewing configuration (e.g., for troubleshooting), always generate
Read Only credentials instead of granting full administrative access.