How It Works: Asynchronous Policy Deployment
When you create or update a Control Plane Policy, the changes are not applied to your devices instantaneously. Instead, SDX uses a secure and resilient asynchronous workflow to ensure reliable delivery.- Policy Update: You modify a policy in the SDX dashboard.
- Job Dispatch: The platform identifies all sites assigned to that policy and dispatches an individual
policy.updatedevent for each one. - Job Queuing: This event is received by our backend, which creates a unique job for each site. This job contains the full, rendered firewall configuration based on the policy.
- Device Polling & Execution: The next time a device checks in with the SDX platform (typically within 30 seconds), it receives the pending job, applies the new firewall rules, and reports back on the outcome.
The Default Policy: Your Security Safety Net
Your Altostrat workspace includes a Default Control Plane Policy out of the box. This policy serves two critical functions:- Secure by Default: When a new device is onboarded, it is automatically assigned the Default Policy. This policy provides a secure starting point by allowing management access only from private RFC1918 IP ranges (
10.0.0.0/8,172.16.0.0/12,192.168.0.0/16) and from Altostrat’s own cloud IPs, while denying all other access. - Fallback Protection: If you delete a custom policy, any sites assigned to it are automatically reassigned to the Default Policy. This prevents devices from being left in an unsecured state with no management firewall.
How to Create and Manage Policies
The workflow involves creating a policy, defining its rules, and then assigning it to the relevant sites.How to Create a Custom Policy
1
1. Navigate to Control Plane Policies
In the SDX dashboard, go to Policies → Control Plane. You will see a list of your existing policies.

2
2. Add a New Policy
Click + Add Policy to open the configuration modal. Provide a descriptive Name for your policy, such as “Read-Only Access” or “Corporate HQ Security”.
3
3. Configure and Save the Policy
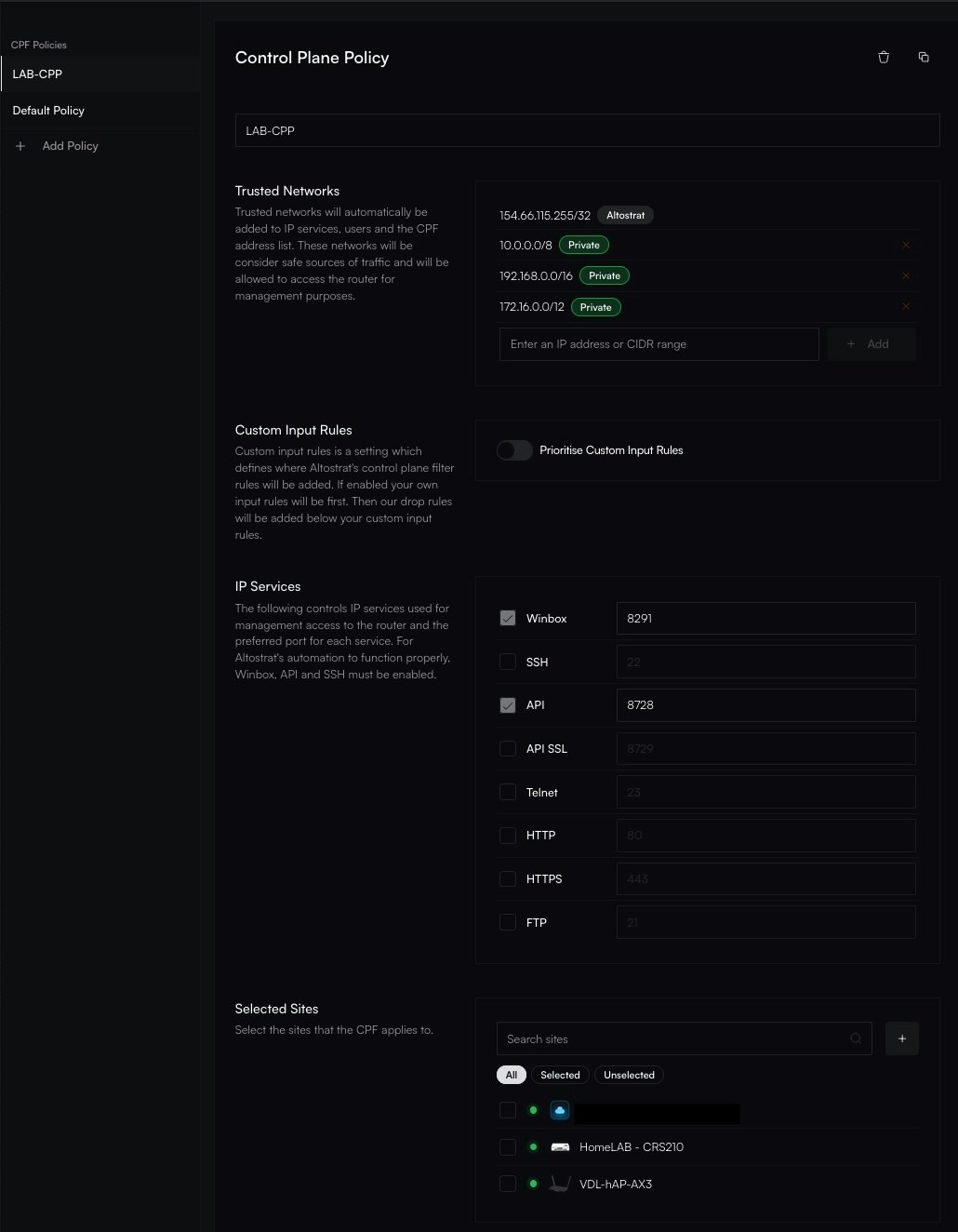
Define the rules for your policy using the available settings. See the Policy Configuration Options section below for a detailed explanation of each field.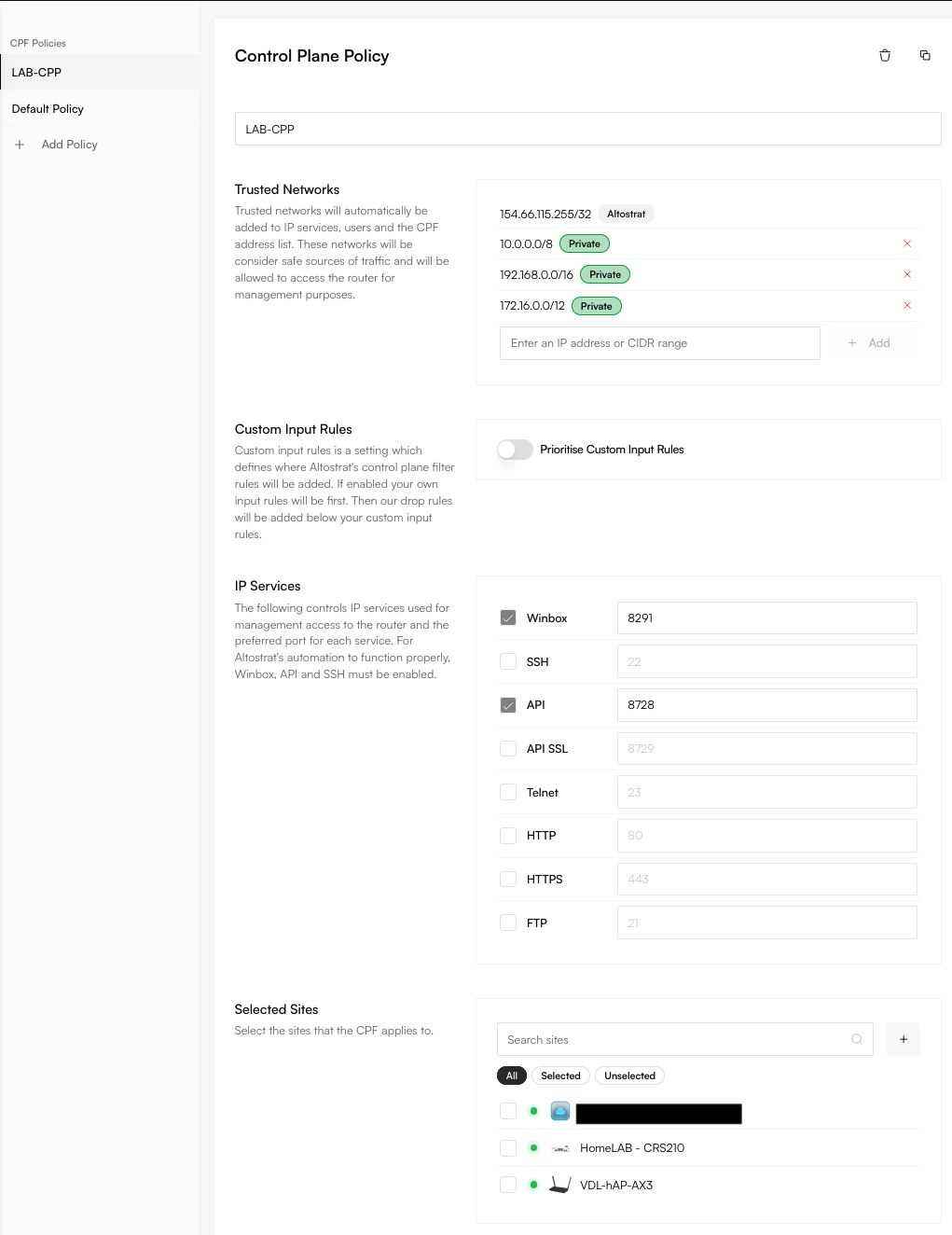
- Add Trusted Networks (CIDRs).
- Enable or disable IP Services and set their ports.
- Toggle Custom Input Rules to manage rule precedence.

How to Assign a Policy to Sites
A Control Plane Policy has no effect until it is assigned to one or more sites.- Navigate to the policy list and click on the policy you wish to assign.
- In the policy editor, go to the Sites tab.
- Select the sites you want this policy to apply to from the list of available sites.
- Click Save. A
policy.updatedjob will be dispatched to all newly assigned (and any removed) sites to update their configuration.
Policy Configuration Options
Trusted Networks
This is the primary IP whitelist for your policy. Only traffic originating from IP addresses or CIDR ranges in this list will be allowed to access the management services defined below. All other traffic will be dropped by default.Best Practice: Keep this list as restrictive as possible. Include your corporate office’s static IP, your home IP, or a management VPN’s IP range.
IP Services
This section allows you to enable or disable specific MikroTik management services and define their listening ports. The networks defined in Trusted Networks are automatically applied to all enabled services.
- WinBox: Port
8291by default. - API: Port
8728by default. - SSH: Port
22by default.
Custom Input Rules
This advanced setting controls how your SDX policy interacts with any pre-existing, manually configured firewall rules on a device.
- Disabled (Default & Recommended): The Altostrat policy takes full precedence. A
drop allrule is placed at the end of the input chain, meaning only traffic explicitly allowed by this policy is permitted. This provides the most secure and predictable configuration. - Enabled: Your device’s existing
inputchain rules are processed before the Altostratdrop allrule. This allows you to maintain custom firewall rules for specific edge cases while still benefiting from the centralized policy for management access.
Best Practices
Principle of Least Privilege
Only allow access from the specific IP networks that absolutely need it. If a service like SSH is not part of your management workflow, disable it in the policy.
Centralize, Don't Deviate
Avoid making one-off firewall changes directly on devices. Instead, create a new, more specific policy in SDX and assign it to the relevant site(s). This maintains a single source of truth and prevents configuration drift.
Layer Your Security
Use Control Plane Policies as your foundational security layer. Combine them with features like Secure Remote Access for on-demand access and Security Groups for data plane traffic.